There’s more to email than just sending and receiving emails. Aside from setting up clients (e.g. desktops, laptops, phones, and tablets), an increasing number of third-party apps are involved. I’ve written this article to help me remember how to set up exchange online servers to handle transactional emails.
Typical scenarios may be forwarding contact forms by email or configuring a CRM system to send emails.
The solution used to be setting up SMTP AUTH client authentication using a username and password. This still works in some circumstances but is prone to failure. A growing part of my business is managing websites and taking on the management of emails.
The exchange online plans from Microsoft or Gmail Suite are ideal for this purpose.
Conditional Access policies
A Google (or Bing!) web search for help setting up SMTP access for accounts suggests that checking that SMTP access has been allowed at the user level will solve authentication problems. And sometimes it does.
As of February 2021, Microsoft will allow existing tenant accounts of exchange online plans to continue using SMTP Auth, but by default, new accounts and tenants will stop using insecure methods.
Authentication will be refused citing “error message: 535: 5.7.3” digging deeper will show:
Access has been blocked by Conditional Access policies. The access policy does not allow token issuance.
MICROSOFT exchange team
How to set up an application to us Office 365
The Microsoft Docs for setting up authentication are (at first glance) confusing, but in fairness, they’re just trying to keep up with a changing situation covering a multitude of scenarios.
There are three options, the first of which is “recommended”. However, it is not possible to set this up on new accounts. A July update explains the background, with an update in February to modify the plan due to the Covid pandemic’s effects.
Microsoft Security Defaults
So, the recommended solution is not possible on new accounts unless the Microsoft Security Defaults have been disabled.
The security defaults are accessed via the azure portal, under properties:
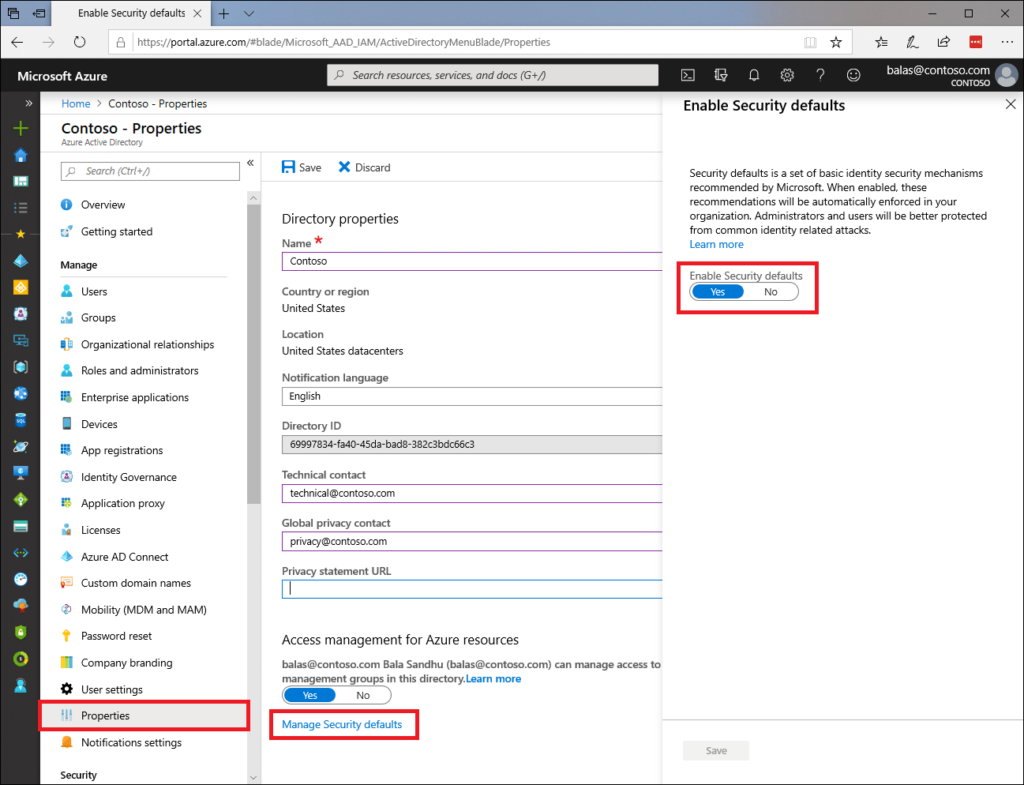
Unfortunately, this can only be applied at the account level, and while it does work, it can’t be a good idea to disable a security policy. Not least as Microsoft are clearly looking to depreciate insecure methods of accessing SMTP servers, what works now may break at some point in the future.
How to set up direct send on a WordPress site using Microsoft Exchange Server
The instructions provided by Microsoft docs are clearly written and do work. Direct send (option 2) requires changes to the DNS records, but nothing major.
This solution works when sending an email from an application (e.g. website) where the email is addressed to someone within your organisation. It won’t work if trying to deliver to external recipients like Gmail.
You can’t use the built-in email handler for WordPress, so (in my view) the best plugin to use is post-SMTP which you can download from the WordPress repository. Don’t use the auto-configuration tool. Instead, click on “Show All Settings”
Under the account tab add your endpoint in the Outgoing Mail Server Hostname box, and 25 in the Server Port box.
You have to add the “from email address” in the account tab, and the message tab.
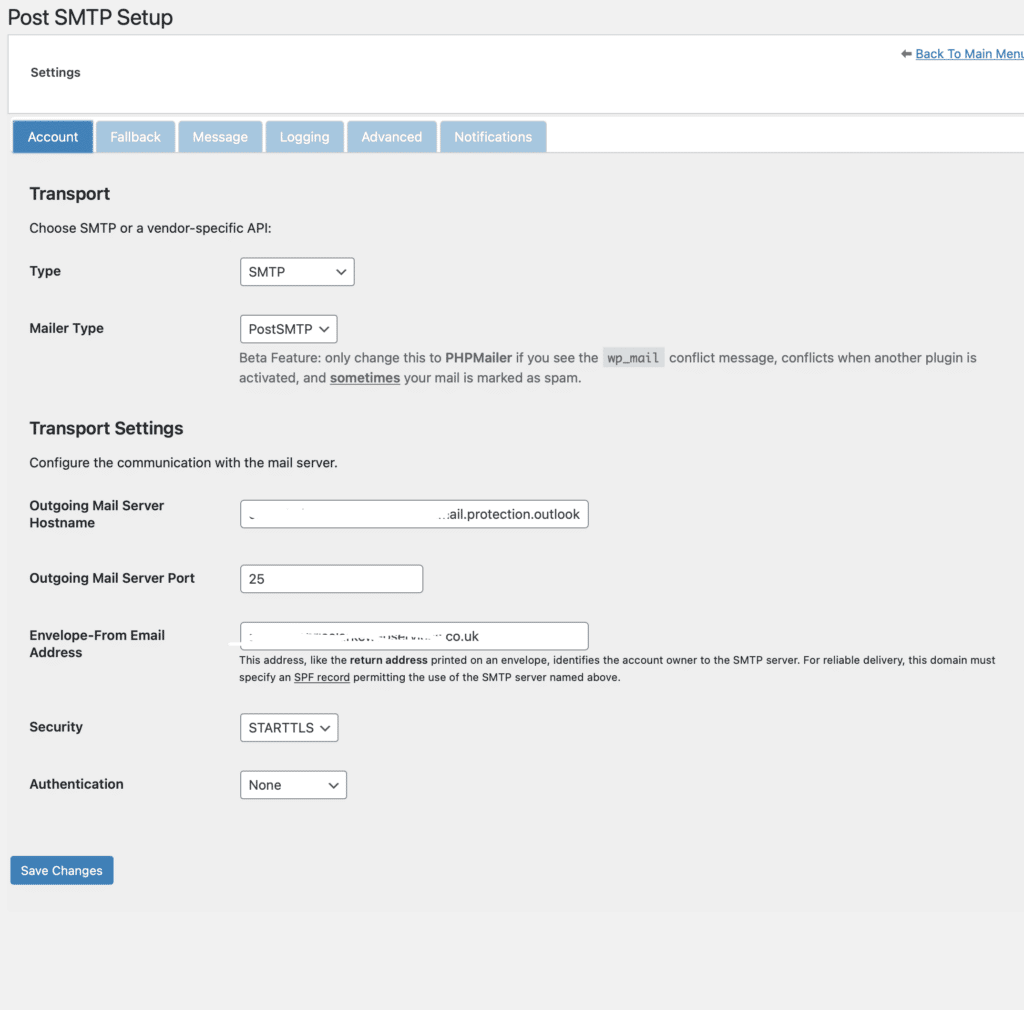
Send a test mail and all should be good!
For completeness. The third option involves setting up a connector app to handle authentication. The WordPress plugin mentioned above does allow for this, and it does work. However, if you don’t have access to the portal or domain settings, there will be a lot of liaising with client IT managers.



